n00bz CTF 2022 writeups - RE
Challenge 01- xorxorxor
this is an ELF file that asks for the flag when we execute it:
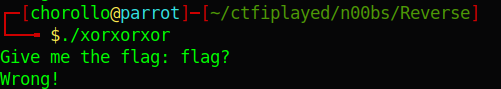
let’s use IDA to decompile and see how the flag is checked.
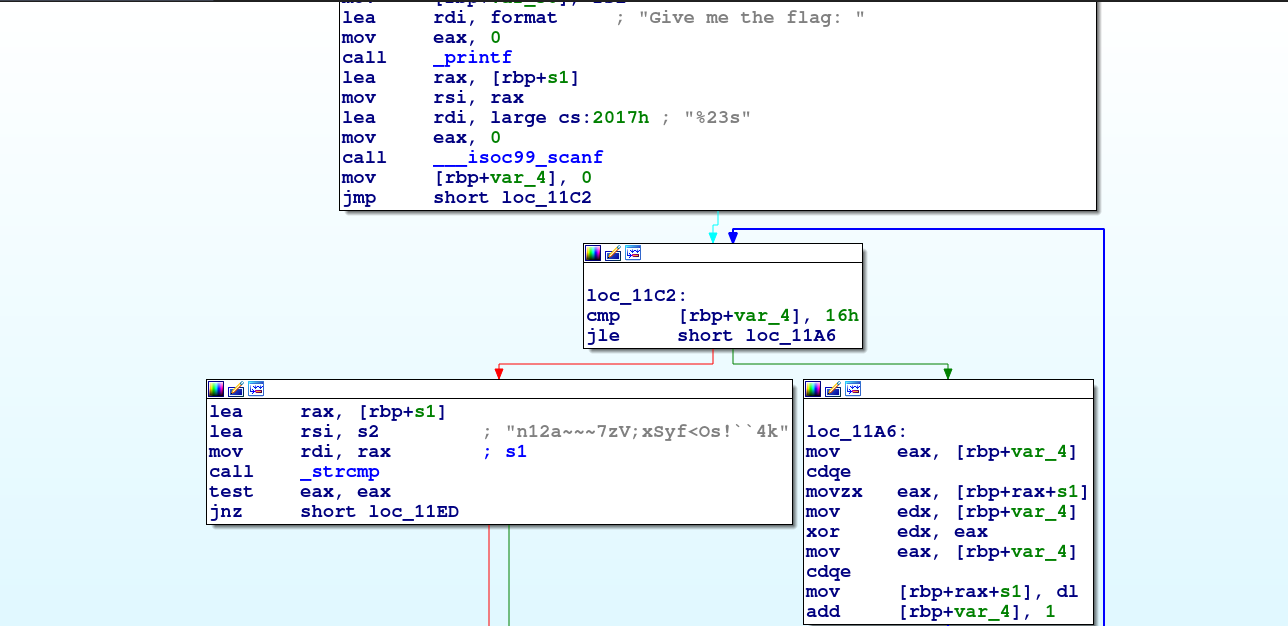
as we can see above, it will do the steps:
- read up to 23 characters (length of the flag+1).
- uses var_4 as a counter that is incremented every time and XORed with a flag character.
- compares the final string with the string n12a~~~7zV;xSyf<Os!``4k.
in order to reverse this I wrote the following script:
s = 'n12a~~~7zV;xSyf<Os!``4k'
for i in range(23):
print(chr(ord(s[i])^i),end='')
Flag: n00bz{x0r_1s_th3_b3st!}
Challenge 02- encryption_with_matrices
In this challenge we are provided with a python script and a resultant cipher text
flag = 'REDACTED'
rand = 'ԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹԹ'
def str_to_matrix(string):
for i in range(2):
letter = ord(string)
flag_mat = [letter,letter]
return flag_mat
final_flag_matrix = []
for i in flag:
final_flag_matrix.append(str_to_matrix(i))
leet_matrix = []
for i in rand:
leet_matrix.append(str_to_matrix(i))
enc_flag_matrix = []
for i in final_flag_matrix:
x = int(i[0]) * int(i[1])
enc_flag_matrix.append(x)
enc_leet_matrix = []
for i in leet_matrix:
y = int(i[0]) * int(i[1])
enc_leet_matrix.append(y)
print(f'leet={enc_leet_matrix}')
print('='*80)
final_ct = []
for i in range(len(enc_leet_matrix)):
final_ct.append(enc_leet_matrix[i]*enc_flag_matrix[i])
print(f'ct={final_ct}')
#ct=[21629584900, 4118558976, 4118558976, 17167812676, 26606176996, 27044131401, 5407396225, 19334346304, 4291953169, 23640600025, 16132810225, 23640600025, 17519963769, 19334346304, 4649466969, 21238107289, 4649466969, 16132810225, 24053528464, 4118558976, 4118558976, 20465877481, 16132810225, 21238107289, 4649466969, 16132810225, 21238107289, 4118558976, 23231246724, 4649466969, 16132810225, 24053528464, 19334346304, 4833586576, 21629584900, 16132810225, 18597867876, 4291953169, 24890110756, 4649466969, 16132810225, 19334346304, 4118558976, 24470032041, 23231246724, 23640600025, 16132810225, 24053528464, 4118558976, 16132810225, 21238107289, 4833586576, 20465877481, 4649466969, 16132810225, 4833586576, 21629584900, 17875690000, 16132810225, 5021281321, 16132810225, 21238107289, 4291953169, 21629584900, 24470032041, 24053528464, 4649466969, 23640600025, 16132810225, 24053528464, 4118558976, 16132810225, 23640600025, 4118558976, 20850204816, 24890110756, 4649466969, 16132810225, 25740993600, 8265719056, 8265719056, 27930765625]
after the analysis of this script i was able to know how this actually works:
- final_flag_matrix and leet_matrix are both obtained using str_to_matrix function.
- str_to_matrix just returns a list with 2 elements containing the letter ordinal.
- enc_flag_matrix and enc_leet_matrix are both obtained by multiplying every element by itself (because i[0] and i[1] contains the same value).
- the final_ct is obtained by multiplying every element in enc_flag_matrix by the corresponding one in enc_leet_matrix.
as we already have the enc_leet_matrix (Just run the script once and you’ll get it) we can easily decrypt this cipher, I wrote the following script:
from math import sqrt
leet=[1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569, 1787569]
ct=[21629584900, 4118558976, 4118558976, 17167812676, 26606176996, 27044131401, 5407396225, 19334346304, 4291953169, 23640600025, 16132810225, 23640600025, 17519963769, 19334346304, 4649466969, 21238107289, 4649466969, 16132810225, 24053528464, 4118558976, 4118558976, 20465877481, 16132810225, 21238107289, 4649466969, 16132810225, 21238107289, 4118558976, 23231246724, 4649466969, 16132810225, 24053528464, 19334346304, 4833586576, 21629584900, 16132810225, 18597867876, 4291953169, 24890110756, 4649466969, 16132810225, 19334346304, 4118558976, 24470032041, 23231246724, 23640600025, 16132810225, 24053528464, 4118558976, 16132810225, 21238107289, 4833586576, 20465877481, 4649466969, 16132810225, 4833586576, 21629584900, 17875690000, 16132810225, 5021281321, 16132810225, 21238107289, 4291953169, 21629584900, 24470032041, 24053528464, 4649466969, 23640600025, 16132810225, 24053528464, 4118558976, 16132810225, 23640600025, 4118558976, 20850204816, 24890110756, 4649466969, 16132810225, 25740993600, 8265719056, 8265719056, 27930765625]
for i in range(len(ct)):
print(chr(int(sqrt(ct[i]/leet[i]))),end='')
Flag: n00bz{7h1s_sch3m3_t00k_m3_m0r3_th4n_f1v3_h0urs_t0_m4k3_4nd_5_m1nut3s_t0_s0lv3_xDD}
Challenge 03- Rusted
- this challenge was very easy Idk why was it solved by only 20 people XD.
for this challenge we get a binary and a text file containing the flag but it’s encrypted in some way, and when you run the binary it allows you to enter some characters then encodes and displays them. the contents of message.txt are:
letter of flag 9430560070627282115
letter of flag 8711072749520663930
letter of flag 8711072749520663930
letter of flag 4680303220831814404
letter of flag 9177864784264774521
letter of flag 14370432302296844161
letter of flag 10876706933096536396
letter of flag 1641124248809936433
letter of flag 7778624499091513472
letter of flag 9919528715426463362
letter of flag 11399395809139327099
letter of flag 10876706933096536396
letter of flag 15080230035883566959
letter of flag 3100520403330787916
letter of flag 15080230035883566959
letter of flag 10876706933096536396
letter of flag 2410296170472410220
letter of flag 13401526571666299780
letter of flag 9430560070627282115
letter of flag 14991883211822224068
letter of flag 11399395809139327099
letter of flag 4680303220831814404
letter of flag 1641124248809936433
letter of flag 9919528715426463362
letter of flag 11399395809139327099
letter of flag 9430560070627282115
letter of flag 8711072749520663930
letter of flag 11564734666458609081
letter of flag 11399395809139327099
letter of flag 16569982846051596422
letter of flag 17912736061507007767
letter of flag 13401526571666299780
letter of flag 12092553686027393261
letter of flag 11399395809139327099
letter of flag 14854574485056723277
letter of flag 11082847621557389877
letter of flag 17912736061507007767
letter of flag 12092553686027393261
letter of flag 12092553686027393261
letter of flag 11399395809139327099
letter of flag 17912736061507007767
letter of flag 2410296170472410220
letter of flag 11399395809139327099
letter of flag 10876706933096536396
letter of flag 15080230035883566959
letter of flag 8432937404534019746
letter of flag 1641124248809936433
letter of flag 15080230035883566959
letter of flag 2410296170472410220
letter of flag 11564734666458609081
letter of flag 15080230035883566959
letter of flag 9016360943569037717
letter of flag 11399395809139327099
letter of flag 4680303220831814404
letter of flag 16090572465429601307
letter of flag 11399395809139327099
letter of flag 363766796468165265
letter of flag 1641124248809936433
letter of flag 7144977204516799495
letter of flag 7778624499091513472
letter of flag 7144977204516799495
letter of flag 10876706933096536396
letter of flag 16272553897485981964
So basically we can either reverse engineer the 10 MB binary and obtain the algorithm (which is a BIG PAIN) or simply let the binary encode all possible letters and numbers and then make a dictionary of them and the corresponding letters, finally find the flag letters.
this was my final script:
s = {'a':7144977204516799495,
'b':4680303220831814404,
'c':14854574485056723277,
'd':9016360943569037717,
'e':9288996555440648771,
'f':10886613961911501365,
'g':14991883211822224068,
'h':11082847621557389877,
'i':8098767115281790549,
'j':16569982846051596422,
'k':14686487834749970899,
'l':12092553686027393261,
'm':16417988931411928334,
'n':9430560070627282115,
'o':4354630192292130566,
'p':6716708359989895925,
'q':8432937404534019746,
'r':10876706933096536396,
's':2410296170472410220,
't':11564734666458609081,
'u':1641124248809936433,
'v':3100520403330787916,
'w':2477510535098418509,
'x':1831594888791778237,
'y':16090572465429601307,
'z':9177864784264774521,
'1':13401526571666299780,
'2':15821950311934020977,
'3':15080230035883566959,
'4':17912736061507007767,
'5':7778624499091513472,
'6':10810294657332723507,
'7':9919528715426463362,
'8':3209422213365730399,
'9':13887348327686894507,
'0':8711072749520663930,
'_':11399395809139327099,
'!':5455878505379436227,
'?':9127593294263825240,
'}':16272553897485981964,
'{':14370432302296844161,
'Q':363766796468165265,
}
flag = [9430560070627282115,8711072749520663930,8711072749520663930,4680303220831814404,9177864784264774521,14370432302296844161,10876706933096536396,1641124248809936433,7778624499091513472,9919528715426463362,11399395809139327099,10876706933096536396,15080230035883566959,3100520403330787916,15080230035883566959,10876706933096536396,2410296170472410220,13401526571666299780,9430560070627282115,14991883211822224068,11399395809139327099,4680303220831814404,1641124248809936433,9919528715426463362,11399395809139327099,9430560070627282115,8711072749520663930,11564734666458609081,11399395809139327099,16569982846051596422,17912736061507007767,13401526571666299780,12092553686027393261,11399395809139327099,14854574485056723277,11082847621557389877,17912736061507007767,12092553686027393261,12092553686027393261,11399395809139327099,17912736061507007767,2410296170472410220,11399395809139327099,10876706933096536396,15080230035883566959,8432937404534019746,1641124248809936433,15080230035883566959,2410296170472410220,11564734666458609081,15080230035883566959,9016360943569037717,11399395809139327099,4680303220831814404,16090572465429601307,11399395809139327099,363766796468165265,1641124248809936433,7144977204516799495,7778624499091513472,7144977204516799495,10876706933096536396,16272553897485981964]
def get_key(val):
for key, value in s.items():
if val == value:
return key
for i in flag:
print(get_key(i),end='')
Flag: n00bz{ru57_r3v3rs1ng_bu7_n0t_j41l_ch4ll_4s_r3qu3st3d_by_Qua5ar}
Challenge 04- Unknown Language
this challenge gives us a disassembled python code and a result.txt file which has the encrypted flag. disassembled code:
2 0 LOAD_NAME 0 (open)
2 LOAD_CONST 0 ('flag.txt')
4 CALL_FUNCTION 1
6 LOAD_METHOD 1 (read)
8 CALL_METHOD 0
10 STORE_NAME 2 (flag)
3 12 LOAD_NAME 0 (open)
14 LOAD_CONST 1 ('results.txt')
16 LOAD_CONST 2 ('w')
18 CALL_FUNCTION 2
20 STORE_NAME 3 (f)
4 22 LOAD_NAME 4 (range)
24 LOAD_NAME 5 (len)
26 LOAD_NAME 2 (flag)
28 CALL_FUNCTION 1
30 CALL_FUNCTION 1
32 GET_ITER
>> 34 FOR_ITER 96 (to 132)
36 STORE_NAME 6 (i)
5 38 LOAD_NAME 7 (input)
40 LOAD_CONST 3 ('Enter the flag: \n')
42 CALL_FUNCTION 1
44 STORE_NAME 8 (x)
6 46 LOAD_NAME 3 (f)
48 LOAD_METHOD 9 (write)
50 LOAD_NAME 10 (str)
52 LOAD_CONST 4 (5)
54 LOAD_NAME 11 (ord)
56 LOAD_NAME 2 (flag)
58 LOAD_NAME 6 (i)
60 BINARY_SUBSCR
62 CALL_FUNCTION 1
64 BINARY_POWER
66 LOAD_NAME 12 (int)
68 LOAD_NAME 8 (x)
70 CALL_FUNCTION 1
72 BINARY_SUBTRACT
74 CALL_FUNCTION 1
76 LOAD_CONST 5 ('\n')
78 BINARY_ADD
80 CALL_METHOD 1
82 POP_TOP
7 84 LOAD_CONST 4 (5)
86 LOAD_NAME 11 (ord)
88 LOAD_NAME 2 (flag)
90 LOAD_NAME 6 (i)
92 BINARY_SUBSCR
94 CALL_FUNCTION 1
96 BINARY_POWER
98 LOAD_NAME 12 (int)
100 LOAD_NAME 8 (x)
102 CALL_FUNCTION 1
104 BINARY_SUBTRACT
106 LOAD_CONST 6 (0)
108 COMPARE_OP 2 (==)
110 POP_JUMP_IF_FALSE 34
8 112 LOAD_NAME 13 (print)
114 LOAD_CONST 7 ('Correct letter ')
116 LOAD_NAME 2 (flag)
118 LOAD_NAME 6 (i)
120 BINARY_SUBSCR
122 FORMAT_VALUE 0
124 BUILD_STRING 2
126 CALL_FUNCTION 1
128 POP_TOP
130 JUMP_ABSOLUTE 34
>> 132 LOAD_CONST 8 (None)
134 RETURN_VALUE
result.txt:
77037197775489434122239117703397092741524065928615527809597551822662353515620,3552713678800500929355621337890620,3552713678800500929355621337890620,315544362088404722164691426113114491869282574043609201908111572265620,18807909613156600127499784595555930845098648908353400344140027300454676151275634765620,94039548065783000637498922977779654225493244541767001720700136502273380756378173828120,48148248609680896326399448564623182963452541205384704880998469889163970947265620,39443045261050590270586428264139311483660321755451150238513946533203120,30092655381050560203999655352889489352157838253365440550624043680727481842041015620,444089209850062616169452667236328120,240741243048404481631997242823115914817262706026923524404992349445819854736328120,17763568394002504646778106689453120,77037197775489434122239117703397092741524065928615527809597551822662353515620,986076131526264756764660706603482787091508043886278755962848663330078120,2524354896707237777317531408904915934954260592348873615264892578120,150463276905252801019998276764447446760789191266827202753120218403637409210205078120,17763568394002504646778106689453120,1203706215242022408159986214115579574086313530134617622024961747229099273681640620,4930380657631323783823303533017413935457540219431393779814243316650390620,2524354896707237777317531408904915934954260592348873615264892578120,3081487911019577364889564708135883709660962637144621112383902072906494140620,3552713678800500929355621337890620,986076131526264756764660706603482787091508043886278755962848663330078120,63108872417680944432938285222622898373856514808721840381622314453120,48148248609680896326399448564623182963452541205384704880998469889163970947265620,17763568394002504646778106689453120,1203706215242022408159986214115579574086313530134617622024961747229099273681640620,4930380657631323783823303533017413935457540219431393779814243316650390620,15407439555097886824447823540679418548304813185723105561919510364532470703120,240741243048404481631997242823115914817262706026923524404992349445819854736328120,2524354896707237777317531408904915934954260592348873615264892578120,150463276905252801019998276764447446760789191266827202753120218403637409210205078120,4930380657631323783823303533017413935457540219431393779814243316650390620,2220446049250313080847263336181640620,1203706215242022408159986214115579574086313530134617622024961747229099273681640620,108420217248550443400745280086994171142578120,2350988701644575015937473074444491355637331113544175043017503412556834518909454345703120
getting back to the code we can notice a pattern:
- read[ flag.txt ], open[ results.txt ], input[ x ], range[means it is using a loop], write[ resultx.txt ]
so from our general understanding of the code we can assume that it open flag.txt reads it, loops through the letters and perform some operations on flag characters, stores the result in result.txt.
what we need to know now is how are the letters encoded?
if we take a look at these lines of code:
6 46 LOAD_NAME 3 (f)
48 LOAD_METHOD 9 (write)
50 LOAD_NAME 10 (str)
52 LOAD_CONST 4 (5)
54 LOAD_NAME 11 (ord)
56 LOAD_NAME 2 (flag)
58 LOAD_NAME 6 (i)
60 BINARY_SUBSCR
62 CALL_FUNCTION 1
64 BINARY_POWER
- this is the code for writing the encoded values to result.txt.
what it is doing is that it takes the flag letter indexed by i which is the counter and perform the following operation:
- 5**flag[i].
- how I knew this was a power? take a look at line 64 BINARY_POWER.
and then writes the number to result.txt.
so to obtain the flag I wrote the script:
from math import log
s = [77037197775489434122239117703397092741524065928615527809597551822662353515620,3552713678800500929355621337890620,3552713678800500929355621337890620,315544362088404722164691426113114491869282574043609201908111572265620,18807909613156600127499784595555930845098648908353400344140027300454676151275634765620,94039548065783000637498922977779654225493244541767001720700136502273380756378173828120,48148248609680896326399448564623182963452541205384704880998469889163970947265620,39443045261050590270586428264139311483660321755451150238513946533203120,30092655381050560203999655352889489352157838253365440550624043680727481842041015620,444089209850062616169452667236328120,240741243048404481631997242823115914817262706026923524404992349445819854736328120,17763568394002504646778106689453120,77037197775489434122239117703397092741524065928615527809597551822662353515620,986076131526264756764660706603482787091508043886278755962848663330078120,2524354896707237777317531408904915934954260592348873615264892578120,150463276905252801019998276764447446760789191266827202753120218403637409210205078120,17763568394002504646778106689453120,1203706215242022408159986214115579574086313530134617622024961747229099273681640620,4930380657631323783823303533017413935457540219431393779814243316650390620,2524354896707237777317531408904915934954260592348873615264892578120,3081487911019577364889564708135883709660962637144621112383902072906494140620,3552713678800500929355621337890620,986076131526264756764660706603482787091508043886278755962848663330078120,63108872417680944432938285222622898373856514808721840381622314453120,48148248609680896326399448564623182963452541205384704880998469889163970947265620,17763568394002504646778106689453120,1203706215242022408159986214115579574086313530134617622024961747229099273681640620,4930380657631323783823303533017413935457540219431393779814243316650390620,15407439555097886824447823540679418548304813185723105561919510364532470703120,240741243048404481631997242823115914817262706026923524404992349445819854736328120,2524354896707237777317531408904915934954260592348873615264892578120,150463276905252801019998276764447446760789191266827202753120218403637409210205078120,4930380657631323783823303533017413935457540219431393779814243316650390620,2220446049250313080847263336181640620,1203706215242022408159986214115579574086313530134617622024961747229099273681640620,108420217248550443400745280086994171142578120,2350988701644575015937473074444491355637331113544175043017503412556834518909454345703120]
for i in s:
print(chr(int(log(i,5))),end='')
Flag: n00bz{rev3s1ng_w1th_l0gar1thms_wh4t?}
Challenge 05- Cookie Clicker
this is some sort of a game where we need to have as much clicks we can on the cookie button.
I was quite confused at the beginning and didn’t know how can I get the flag or what should I do?, but after I saw the description I got a clear idea in my head about the process of solving this
Description: I wanna reach a million cookies!
HMMMMMMMMMMM, but I can’t click a million time on the cookie!
when I run the binary for the first time I noticed that it drops an excel file that contains the statistics for the player.
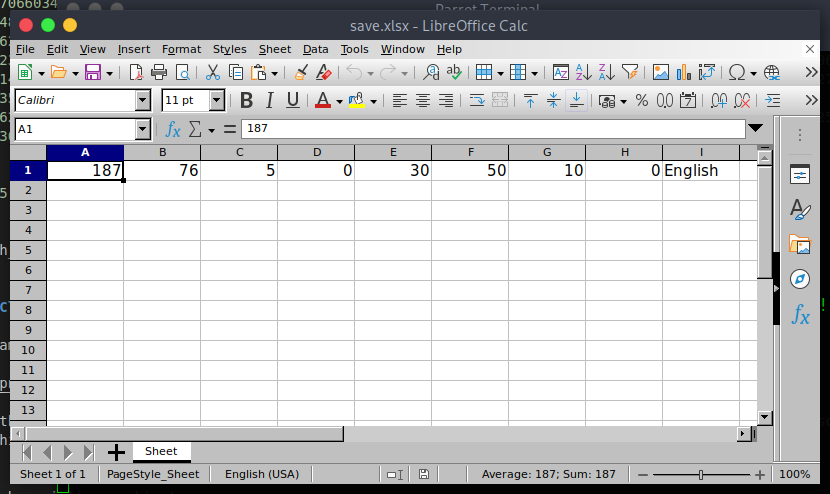
I immediately thought of changing the clicks value to a large number then re-opened the game.
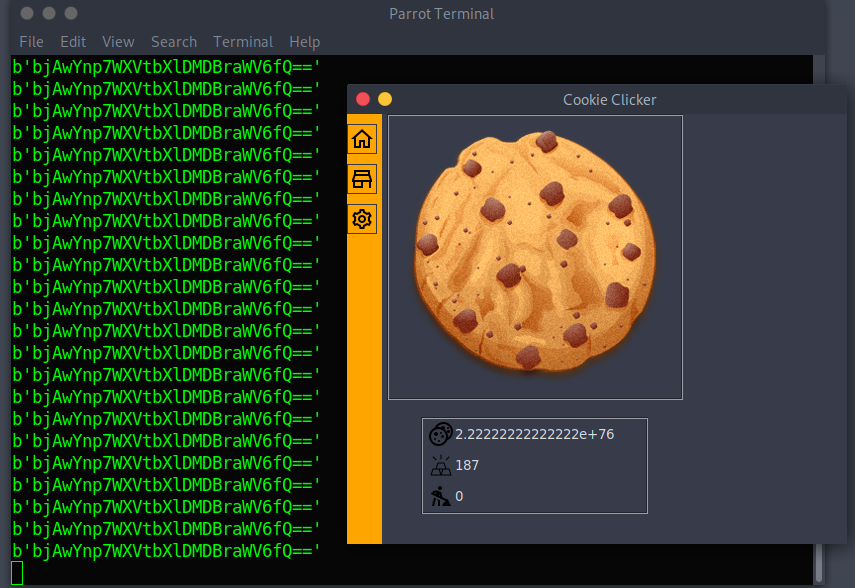
and fair enought! I got a base64 encrypted flag!
Flag: n00bz{YummyC00kiez}
